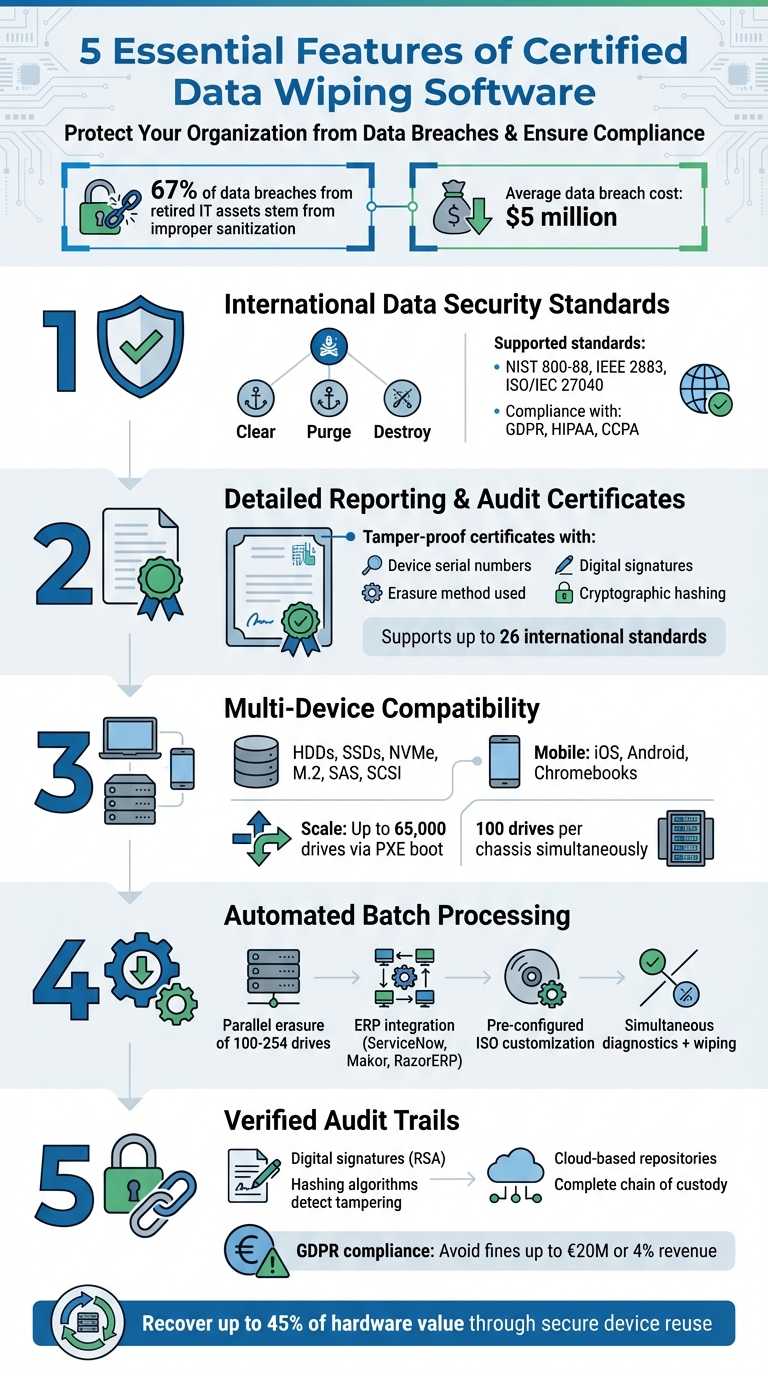
Top 5 Features in Certified Data Wiping Software
Certified data wiping software is essential for securely erasing sensitive information from retired devices, reducing risks of data breaches, and ensuring compliance with strict regulations like GDPR, HIPAA, and CCPA. Unlike basic deletion methods, these tools offer advanced techniques and detailed documentation to protect organizations from legal and financial consequences. Here’s a quick overview of the top features to look for:
- Compliance with International Standards: Supports NIST 800-88, IEEE 2883, and other recognized guidelines for secure data removal.
- Detailed Reporting: Provides tamper-proof Certificates of Data Destruction with key details like serial numbers and erasure methods.
- Multi-Device Compatibility: Works with a variety of devices, including HDDs, SSDs, servers, mobile devices, RAID arrays, and more.
- Automated Batch Processing: Enables parallel erasure of multiple devices, saving time and ensuring consistency.
- Verified Audit Trails: Uses digital signatures and hashing to maintain secure, traceable records of all erasure activities.
These features not only protect sensitive data but also support safe device reuse or resale, helping organizations recover up to 45% of hardware value. Certified data wiping tools are a critical investment for security, compliance, and operational efficiency.
5 Essential Features of Certified Data Wiping Software
How To Completely Wipe Drives ~ Secure Wipe Hard Drives | SSD to NIST DoD - BitRaser | Nico Knows

1. Meets International Data Security Standards
When evaluating data wiping software, one of the most critical features to consider is compliance with internationally recognized standards. Different data wiping methods vary in effectiveness, and choosing the wrong one can expose your organization to data breaches or regulatory penalties. Certified software should align with modern standards like NIST 800-88, IEEE 2883, and ISO/IEC 27040. These standards ensure reliable data protection across various storage devices.
In the United States, NIST 800-88 is often considered the benchmark for media sanitization. Updated on September 26, 2025, this standard outlines three levels of sanitization: Clear (overwriting user data), Purge (using firmware commands or cryptographic erasure), and Destroy (physical destruction). Its flexibility makes it applicable to all types of media and helps organizations meet GDPR's "right to erasure" requirements.
For flash-based storage like SSDs and NVMe drives, IEEE 2883 addresses specific challenges such as wear leveling and over-provisioning. Legacy methods like the DoD 5220.22-M standard, which relies on multiple overwrite passes, are not only ineffective for SSDs but can also harm the hardware.
The consequences of improper data sanitization can be severe. For example, in November 2022, SAP faced a major issue when one of four missing SSDs from its Walldorf, Germany data center appeared for sale on eBay. The drive, which had not been properly sanitized, contained personal records of around 100 employees.
In addition to securely wiping data, thorough documentation is a must. Certified software should provide audit-ready certificates with key details such as the device's serial number, the specific standard applied (e.g., "NIST 800-88 Purge"), verification results, and a digital signature. These certificates act as legally defensible proof of your organization’s efforts to protect sensitive data - an essential safeguard when the global average cost of a data breach hovers around $5 million.
2. Detailed Reporting and Audit Certificates
Erasing data is just one part of the process. Certified wiping software must also produce tamper-proof certificates that confirm data has been completely erased. These certificates are more than just documentation - they’re a legal safeguard during compliance audits, regulatory inspections, or internal reviews. Without them, organizations risk fines and liability claims because there’s no concrete proof that sensitive data has been destroyed. These certificates provide a detailed account of the erasure process.
"The certificate serves as a comprehensive record of the 'who, what, where, when, and how' of data erasure." – Blancco
A compliance-ready certificate includes key details like the device's serial number, the erasure method used (e.g., "NIST 800-88 Purge"), the software version, the erasure status, the technician's ID, and a digital signature. To ensure authenticity, cryptographic hashes are used, and any tampering is flagged by tools like the Blancco Management Console. This tamper-proof design is essential for meeting regulations such as HIPAA, SOX, or GDPR.
Modern reporting tools go a step further, offering insights beyond just erasure confirmation. For instance, some software provides hardware diagnostics, S.M.A.R.T. stats, and UEM status checks (e.g., Apple MDM or Microsoft Autopilot). These features help prevent accidental resale or reuse of devices with active cloud locks. Many enterprise solutions even include color-coded visual indicators - green for successful erasure and red for failures.
For organizations managing large volumes of devices, centralized management becomes crucial. Cloud-based repositories or integrations with ERP and ITSM tools like ServiceNow can automate the storage and tracking of thousands of certificates. This automation not only reduces manual errors but also makes it easy to retrieve records during unexpected compliance checks. Additionally, some software supports up to 26 international erasure standards and allows customization with up to 20 extra fields to meet specific organizational needs.
3. Works with Multiple Device Types
Today's IT setups are anything but uniform. Most organizations juggle a mix of hardware, from Dell servers in data centers to MacBooks powered by Apple Silicon for executives, Android tablets for field teams, and even older workstations with legacy PATA hard drives. Certified data wiping software needs to handle this wide range of devices. Top-tier solutions are equipped to support everything - from standard HDDs and SSDs to more specialized interfaces like NVMe, M.2, SAS, and SCSI.
Beyond handling diverse devices, enterprise environments demand tools that are scalable and work seamlessly across systems. These solutions should integrate with networks, iSCSI devices, and RAID arrays while enabling large-scale erasure. For example, they might support wiping up to 65,000 drives via PXE boot or simultaneously erasing 100 drives within a single chassis. This level of scalability is vital for IT asset disposition programs and for retiring equipment in data centers efficiently.
Mobile devices bring their own set of requirements. Leading software solutions can automatically detect drive types and apply the best wipe policies to ensure thorough data removal. They also extend support to mobile devices like iOS and Android smartphones, Chromebooks, USB flash drives, and SD cards. Additionally, they help identify devices enrolled in management systems, ensuring locked devices don’t slip back into the resale or reuse stream.
Another critical feature is the ability to access hidden areas of drives - like HPA, DCO, and remapped sectors - which standard formatting often skips. For older ATA drives, the software should be capable of clearing BIOS freeze locks to execute ATA Secure Erase. Without such functionality, organizations risk incomplete data removal, leaving them exposed to compliance violations or security issues.
Recycle Electronics Responsibly
Schedule a pickup or drop off your e-waste at Rica Recycling to ensure eco-friendly, secure, and compliant electronics recycling in the Bay Area.
Schedule Now4. Automated Batch Processing
Manually configuring hundreds - or even thousands - of devices can create a major bottleneck in operations. Automated batch processing solves this issue by enabling parallel erasure, which reduces downtime and boosts efficiency. Once compliance and device support are confirmed, automation ensures consistent results across the board. It’s a logical step when choosing certified data-wiping solutions.
The most robust tools allow drives to be wiped over a network using PXE boot, while smaller setups can handle anywhere from 100 to 254 drives at the same time. This flexibility is especially important for IT asset disposition (ITAD) facilities that deal with bulk equipment from corporate upgrades or data center decommissions. Automation doesn’t just save time - it also standardizes the process. ISO customization features let administrators pre-configure erasure methods to align with NIST 800-88 standards and “lock” those settings across devices. This eliminates errors and ensures every device follows the same protocol.
Integration with existing ERP and asset management systems takes things a step further by simplifying the certification process. Top-tier software can connect directly to ITAD-specific ERPs like Makor ERP and RazorERP, as well as platforms like ServiceNow. This means erasure certificates are automatically linked to asset records, removing the need for manual data entry. For instance, CompuCycle, an ITAD company based in Texas, adopted the BitRaser Drive Eraser Admin Console and achieved full integration with their internal ERP system. This created a smooth, automated workflow for bulk asset disposal.
Some advanced solutions go even further by combining multiple workflows. Instead of running diagnostics separately, high-efficiency software can perform hardware diagnostics and data wiping at the same time, cutting down the processing time for each asset. Additionally, certain platforms offer "wipe-to-reimage" automation, where devices are reimaged for resale immediately after a successful erasure. This eliminates a manual step in the refurbishment process, streamlining operations even more.
5. Verified Audit Trails and Data Integrity
After wiping devices in bulk, the next hurdle is proving that the process was completed and ensuring the records remain intact. Verified audit trails tackle this challenge by using digital signatures and hashing algorithms to secure every erasure report. If even the smallest change occurs, like altering a single character, the system flags it as a discrepancy.
"If even a single comma has changed on the certificate, the Blancco Management Console will detect it during report verification." - David Stegon, Senior Content Writer, Blancco
These secure audit trails go hand-in-hand with thorough erasure processes, creating a stronger guarantee of data integrity. The stakes for getting this right are enormous. For example, in 2022, Morgan Stanley faced a $35 million fine from the SEC after failing to maintain a proper chain of custody during device decommissioning. The result? Decommissioned hard drives with unencrypted customer data were sold at auction. Situations like this are avoidable when audit trails provide a complete record, including key details like:
- Unique device identifiers (e.g., serial numbers, IMEI, or UUID)
- The specific erasure method used (such as NIST Purge)
- Software version, timestamps, and personnel involved
This level of detail ensures an unbroken chain of custody, reducing the risk of exposure.
Detailed documentation also helps prevent regulatory penalties. Poor record-keeping undermines data security, as shown by a 2023 survey where 42% of IT professionals couldn’t confirm complete data erasure. Under GDPR, such mishandling can lead to fines as high as €20 million or 4% of global annual revenue. Certified data wiping software addresses these risks by storing audit trails in centralized, cloud-based repositories - keeping records secure, accessible, and tamper-proof for external audits. For businesses needing professional assistance, data destruction and ITAD services can streamline this documentation process.
When selecting software, insist on serialized proof for each certificate. Certificates lacking specific serial numbers can lead to "process assumptions", where paperwork is issued without actual work being done. To avoid this, ensure certificates are backed by RSA digital signatures, which eliminate manual errors and provide consistent, legally defensible documentation.
Conclusion
Choosing the right certified data wiping software comes down to focusing on five key features: compliance with international standards, detailed reporting with audit certificates, multi-device compatibility, automated batch processing, and verified audit trails. These features not only safeguard organizations from the hefty financial and legal fallout of inadequate data sanitization but also address a critical vulnerability - around 67% of data breaches tied to retired IT assets stem from improper sanitization. With the global average cost of a data breach hovering around $5 million, the stakes couldn't be higher. High-profile cases, like those involving Morgan Stanley and SAP, underscore the real-world risks of mishandling data during device disposal.
But the benefits of certified data wiping go beyond just risk reduction. Properly sanitized devices can reclaim up to 45% of their original value through resale or buyback programs. This approach not only supports hardware reuse but also helps reduce e-waste, a growing priority for organizations committed to ESG goals. For businesses in the San Francisco Bay Area, Rica Recycling offers certified data destruction services as part of their broader IT asset recovery and electronics recycling solutions. Their services include certificates of data destruction and a 100% landfill-free policy, ensuring that businesses, schools, and government agencies meet both security and environmental standards. From secure data wiping to e-waste pickup and IT asset recovery, Rica Recycling provides a responsible and compliant solution for retired devices.
Certified data wiping software isn't just a tool - it's a critical component for protecting sensitive information, boosting asset recovery, and ensuring regulatory compliance. By leveraging these capabilities, organizations can secure their data, maximize the value of retired assets, and support sustainable practices - principles that Rica Recycling is dedicated to delivering.
FAQs
What are the key compliance standards for certified data wiping software?
Certified data wiping software must adhere to established standards to guarantee secure and thorough data removal. One of the most trusted guidelines is NIST Special Publication 800-88 Revision 1. This standard lays out best practices for clearing, purging, and destroying data in a way that prevents recovery. It's widely adopted by both private companies and government agencies across the United States.
Beyond NIST compliance, certifications like NAID AAA and R2 add an extra layer of assurance. These certifications not only validate secure data destruction methods but also highlight responsible recycling practices. Meeting these standards ensures that the software and processes align with strict security and environmental guidelines, offering organizations the confidence and documentation needed for audits and regulatory compliance.
Why is detailed reporting an essential feature in certified data wiping software?
Detailed reporting plays a key role in certified data wiping software by offering clear, verifiable evidence that sensitive information has been securely erased. These reports help organizations comply with regulations, sidestep legal complications, and simplify audits by providing thorough documentation of the data destruction process.
Moreover, detailed reports boost transparency and accountability, ensuring businesses can trust that their data has been managed securely and responsibly. This is especially critical for industries like healthcare, finance, and education, where strict data protection rules are in place.
Why is it important for data wiping software to work with multiple device types?
Having data wiping software that works across multiple devices is a game-changer. It ensures secure erasure on a variety of storage devices - like hard drives, SSDs, NVMe drives, and more. This means businesses can rely on one solution for all their data sanitization needs, cutting down the risk of leaving sensitive data behind due to mismatched tools or methods.
Beyond convenience, this compatibility plays a key role in meeting strict data protection standards, such as NIST 800-88, HIPAA, and GDPR, which demand secure disposal of all data-bearing devices. Plus, it makes life easier for IT teams. They can manage and verify data wiping processes more efficiently, reducing the chance of human error and saving valuable time.
In short, multi-device compatibility doesn’t just boost security and ensure compliance - it also simplifies day-to-day operations for businesses managing a mix of electronic devices.
